Meet your customers' cybersecurity challenges
ASSESS YOUR CUSTOMERS' IT SECURITY MATURITY AND THEIR LEVEL OF RISK EXPOSURE
In your dedicated space, you can use dynamic forms that generates a report with recommendations.
CYBERESIST®< 0 >addresses the challenges faced by MSPs and MSSPs
PROSPECTING: quickly generate initial assessments of your customers or prospects in order to optimise your sales efforts and measure the level of operational security across a range of areas, including Active Directory/Azure, backups, networks, messaging, GDPR, etc. You can then use the reports to improve your conversion rate.
AUTOMATED AUDITS: Manage comprehensive cybersecurity audits for your clients and handle security vulnerability remediation with action plans and recommended solutions.
Why include CYBERESIST® in your offering?
SECURE INFRASTRUCTURE
Hosting in France (OVH).
Constant updates to CVEs.
FULL AUTOMATION
80+ built-in tools.
Audits without manual intervention.
PROFESSIONAL REPORTS
Word, Excel, and PDF formats. Mapping, report, and action plan.
MULTI-TENANT
Multi-tenant platform, easy to operate, grey or white label
PROSPECTING
Integrated prospecting tools based on risk analysis & proactive posture.
INTEGRATIONS
APIs & Webhooks with ITSM/SIEM solutions and alert workflows.
PROSPECTING TOOLS FOR PRE-SALES
01
CYBERESIST® for your prospecting
If you are a Managed Service Provider (MSP or MSSP), you can use CYBERESIST® for your prospecting:
- Engage your leads with requests for quotes
- Identify the services you want to offer as a priority and bring in business with your partners.


02
Dynamic form
Complete a questionnaire and self-assess your IT security maturity – get a report with suggestions for action.

03
The initial diagnosis (passive scan)
CYBERESIST® searches for potential threats on the web.
Forums, social networks, specialised websites and the dark web are analysed to detect mentions of the organisation, data leaks and any vulnerabilities or planned attacks.

03
Pre-Scan results
Research into potential threats and data leaks enables security flaws and risky configurations to be detected, providing a comprehensive view of potential weak points.

04
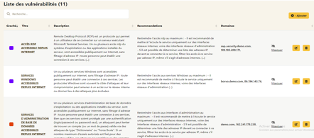
Detailed reports
CYBERESIST® automatically generates a detailed report with recommendations for action plans.
05
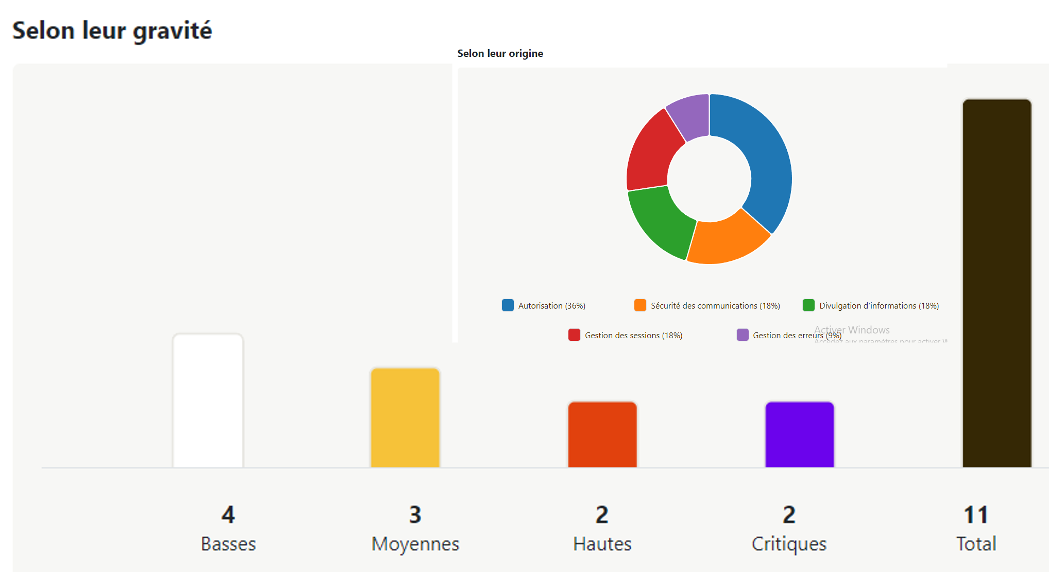
Recommendations by category
CYBERESIST® automatically generates recommendations that you can use directly or pass on to your client.

MSP distributor
List the CYBERESIST solution on your marketplace to sell subscriptions to your MSP customers.
MSP & MSSP
Dedicated resources to optimise the sale of managed security services, with white label reporting.
Solution partner
Our APIs/Webhooks enable integration with other ITSM/SIEM/GRC platforms.
THE BENEFITS OF CYBERESIST®
An all-in-one solution.
When it comes to cybersecurity, you can pro actively protect your customers from digital threats.
Pre-scan, automated report, and recommendations by vulnerability category.
Dynamic questionnaire to assess a company's maturity and level of exposure
For YOUR SALES TEAM: a comprehensive tool for LEAD GENERATION AND CONVERSION.
A solution for all consulting and security professionals.





