Assess security blind spots with CYBERESIST®
ALL-IN-ONE PLATFORM FOR AUDITING YOUR EXTERNAL, INTERNAL AND CLOUD ATTACK SURFACES
CYBERESIST® detects security vulnerabilities and data leaks that hackers can exploit, providing a comprehensive security assessment.
The platform conducts in-depth risk analysis using intelligent tests that highlight attack vectors and proposes a corrective action plan.
MULTI-TENANT SOLUTION
Easy-to-use platform, grey or white label. Customer portal.
SECURE INFRASTRUCTURE
Hosting in France (OVH).
Constant updates to CVEs.
100% AUTOMATED TESTS
80+ integrated tools. Comprehensive testing without manual intervention.
CORRELATION & SORTING
Fewer duplicates and a massive reduction in false positives.
PROFESSIONAL REPORTS
In Word, Excel, and PDF formats with scorecard and action plan.
INTÉGRATION & API
Integrations with your SIEM/ITSM solutions and alert workflows.
FEATURES
01
Attack surface mapping
CYBERESIST® identifies all web applications and services used, including uninventoried or unofficially approved services (Shadow-IT), as well as your internal network.
This mapping provides a better understanding of your IT infrastructure, enhances security, and optimises resource management.

02
Internet monitoring & dark web surveillance
CYBERESIST® searches for potential threats to the company on the web: forums, social networks, specialised sites and the dark web are analysed to detect mentions of the organisation, data leaks, source code leaks, hacked accounts and any vulnerabilities or planned attacks.

03
Scanning of attack surfaces
Over 80 specialised tools analyse in detail the elements accessible via the web, your internal network or the cloud environment. This approach detects vulnerabilities, security flaws and risky configurations, providing a comprehensive view of potential weaknesses.
04
Automated audits with no impact
CYBERESIST® audits do not require any probes, agent installation or event log collection, ensuring rapid implementation with no impact on the performance of your infrastructure or the integrity and anonymity of your sensitive data.
05
Vulnerability Scan
CYBERESIST® performs a vulnerability scan for each detected component, providing detailed analysis and accurate identification of security flaws.
100+ families, correlation and prioritisation.
Fewer duplicates and a massive reduction in false positives.

06
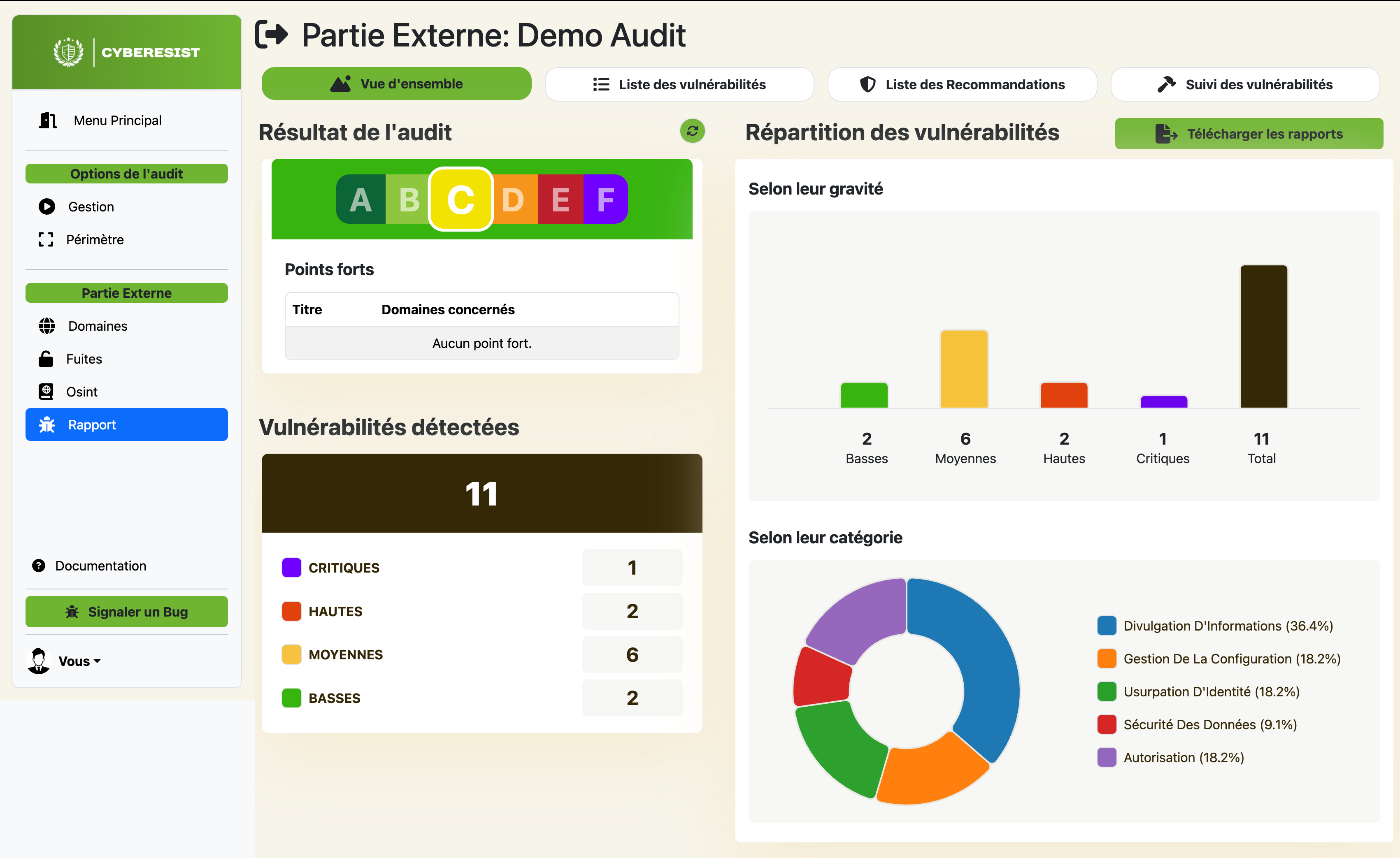
Professional reports & action plan
CYBERESIST® provides comprehensive dashboards with a global view including a scorecard, a management summary facilitating the understanding and communication of results, a detailed list of vulnerabilities with recommended solutions, and remediation tracking.
Reports can be exported in Word, Excel, and PDF formats and can be produced in white label format for MSPs and MSSPs.
07
Measuring developments
After your team or IT manager has implemented the fixes, CYBERESIST® performs a check to verify that the issues have been resolved and to measure progress between audits.
08
Continuous monitoring
CYBERESIST® offers monitoring that includes detection of data leaks, new vulnerabilities, and phishing attacks targeting your users. This constant surveillance allows you to respond quickly to threats and maintain a high level of security.
THE BENEFITS OF CYBERESIST®
Connection to actual data leaks
Unprecedented post-login exploration
Common vulnerabilities
Detection of "untraceable" vulnerabilities
Integrated and adaptive AI
Development of bespoke scenarios
Differentials between 2 scans
Business impact-oriented vision
MSP & MSSP edition
You are an MSP or MSSP and you want to perform regular security checks for your customers.
We offer you the opportunity to operate a dedicated CYBERESIST® instance with your teams, either as a grey or white label solution.
Your customers benefit from a complete cybersecurity solution by working directly with your company.
Generate additional revenue and strengthen your position as a trusted partner.
PROSPECTING
Integrated prospecting tools, risk-based & proactive posture.
CLIENT ONBOARDING
Domains, perimeters, AD, OSINT in just a few minutes.
ORCHESTRATION
Nmap, Nuclei, OpenVAS, ZAP orchestrated according to your playbooks.
They trust us










